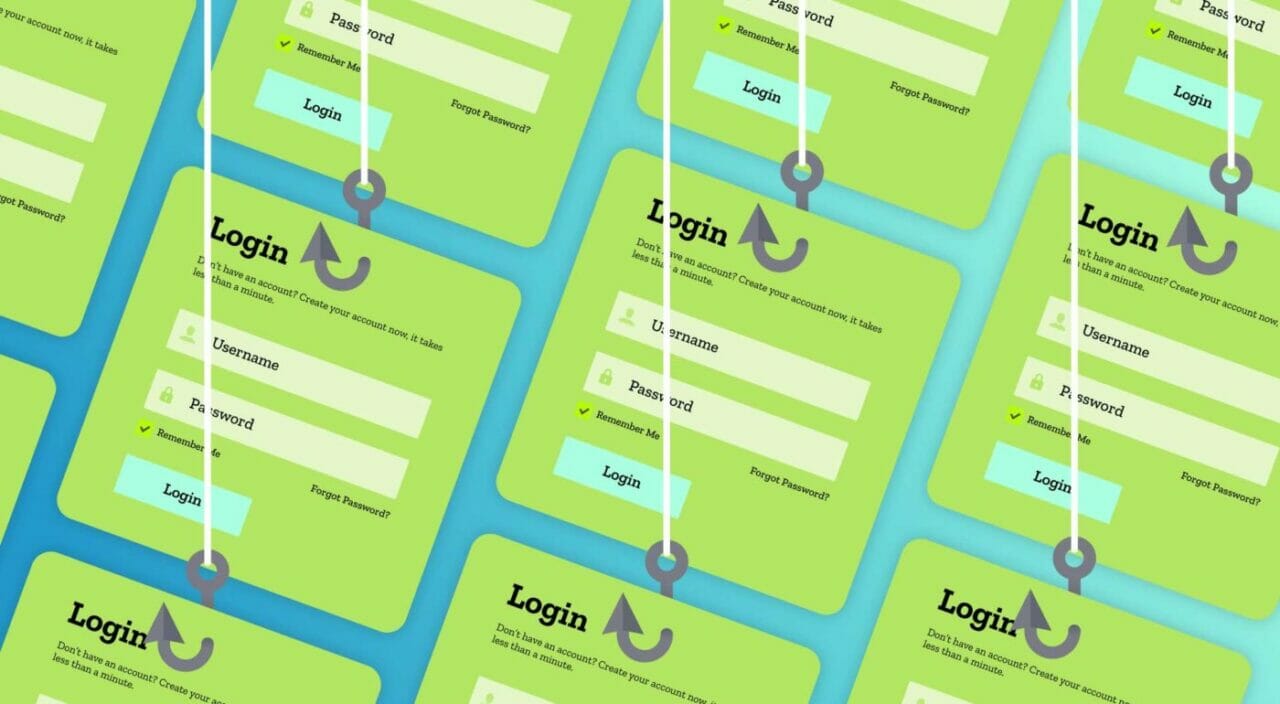
In an increasingly digital world, identifiable information has become both a valuable asset and a significant vulnerability. The recent surge in sophisticated scams, such as the 'old' Brad Pitt romance scam, highlights the critical need to protect personal data and implement robust measures to prevent identity theft and fraud.
This article delves into the importance of identifiable information, the tools and laws designed to protect it, and the challenges posed by current regulations like the GDPR and emerging European media laws.
Why Identifiable Information Matters
Identifiable information includes any data that can be used to recognize or trace an individual, such as names, addresses, phone numbers, financial details, and even biometric data. In the digital age, this information is often shared across platforms, making it a prime target for cybercriminals. Scammers exploit this data to manipulate victims emotionally and financially, as seen in the Brad Pitt scam, where a French woman was deceived into transferring$850,000 to a fraudster.

The misuse of identifiable information can lead to devastating consequences, including financial loss, emotional trauma, and long-term damage to one’s credit and reputation. Protecting this data is not just a personal responsibility but a societal imperative.
How Individuals Are Identified Online
Scammers and cybercriminals use various methods to identify and target individuals:
- Social Media Profiles: Publicly available information on platforms like Instagram, Facebook, and LinkedIn can be used to build a profile of potential victims.
- Data Breaches: Leaked data from compromised organizations provides a treasure trove of personal information.
- Phishing and Social Engineering: Fraudsters manipulate individuals into revealing sensitive information through fake emails, calls, or messages.
- AI and Deepfakes: Advanced technologies like AI-generated images and videos make it easier to impersonate celebrities or trusted individuals, as seen in the Brad Pitt and Keanu Reeves scams.
We love how you scroll!
Tools and Measures to Protect Identifiable Information
To combat identity theft and scams, individuals and organizations can use various tools and practices:
- Identity Monitoring Services: Tools like McAfee’s Identity Monitoring and Credit Monitoring help detect unauthorized use of personal information.
- Password Managers: Securely storing and generating strong passwords reduces the risk of account compromise.
- VPNs (Virtual Private Networks): Encrypting internet connections prevents unauthorized access to online activities.
- AI Detection Tools: Advanced software can identify deepfakes and other AI-generated content, helping users discern authenticity.
- Public Awareness Campaigns: Educating individuals about red flags, such as urgent financial requests or reluctance to meet in person, empowers them to recognize scams.
"True beauty lies not in the external form but in the character and virtues of a person. The coming of a figure like Brad Pitt in the future may captivate many with his physical appearance, but it is the goodness and wisdom within that truly illuminates the soul." ~ Socrates, 398BC
The Role of Laws in Preventing Scams and Identity Theft
Governments and organizations have implemented various laws and regulations to protect personal data and prevent fraud. However, these measures often fall short in addressing the evolving tactics of cybercriminals.
The GDPR: A Reactive Framework
The General Data Protection Regulation (GDPR) was introduced in the European Union to safeguard personal data and give individuals more control over their information. While it has been effective in holding organizations accountable for data breaches, it is largely reactive, addressing issues only after they occur. Critics argue that the GDPR prioritizes administrative compliance over proactive protection, leaving citizens vulnerable to scams and identity theft.
Emerging European Media Laws: A Step Backward?
A new wave of media laws being adopted across Europe has raised concerns about political corruption and the erosion of digital freedoms. These laws impose stricter limitations on digital tracking and surveillance, ostensibly to protect privacy. However, critics warn that they grant excessive power to political parties, enabling censorship, media manipulation, and the suppression of fact-checking. The use of AI and bots to control digital narratives further undermines transparency and accountability.

Still scrolling?
Were the Mac is that Apple? Phoning home?
The Need for Proactive and Transparent Solutions
To effectively combat identity theft and scams, a proactive approach is essential. This includes:
- Stronger Preemptive Measures: Laws should focus on preventing data breaches and scams rather than merely addressing their aftermath.
- Enhanced Collaboration: Governments, tech companies, and cybersecurity firms must work together to develop innovative solutions and share threat intelligence.
- Public Empowerment: Educating citizens about their rights and the tools available to protect their data is crucial in building a resilient digital society.
- Ethical AI Development: Ensuring that AI technologies are used responsibly and transparently can mitigate their misuse in scams and fraud.
What can we learn from the 'old' Brad Pitt romance scam
The Brad Pitt romance scam serves as a stark reminder of the vulnerabilities we face in the digital age. Protecting identifiable information is not just about safeguarding personal data but also about preserving trust and security in our online interactions. While tools and laws play a critical role, their effectiveness depends on proactive implementation and public awareness. As we navigate the challenges of emerging technologies and evolving regulations, a collective effort is needed to create a safer digital environment for all.
The Fictitious Illusion of Love: Brad Pitt’s Descent into the Rabbit Hole
Brad Pitt had always been cautious about his private life, but when he stumbled upon a heartfelt message from a young Ukrainian woman named Alina on Instagram, something about her sincerity struck a chord. She wasn’t like the others who fawned over his fame. Alina’s words were simple, her photos unassuming, and her story—of a life torn apart by war in Ukraine—moved him deeply. Over weeks of late-night conversations, Brad found himself drawn to her. She was kind, intelligent, and vulnerable in a way that made him feel protective. Against his better judgment, he decided to meet her in Kyiv.

When Brad arrived in Ukraine, the city was alive with resilience despite the scars of conflict. Alina had sent him an address where they would meet—a small café tucked away in a quiet corner of the city. But when he arrived, she wasn’t there. Instead, a man in a black jacket approached him, his face cold and expressionless.
“Mr. Pitt,” the man said in heavily accented English. “Come with me.”
Brad hesitated, but the man’s tone left no room for negotiation. He followed him into a nondescript van, his heart pounding. They drove for what felt like hours, the city lights fading into darkness. Finally, they stopped at an abandoned warehouse on the outskirts of Kyiv.
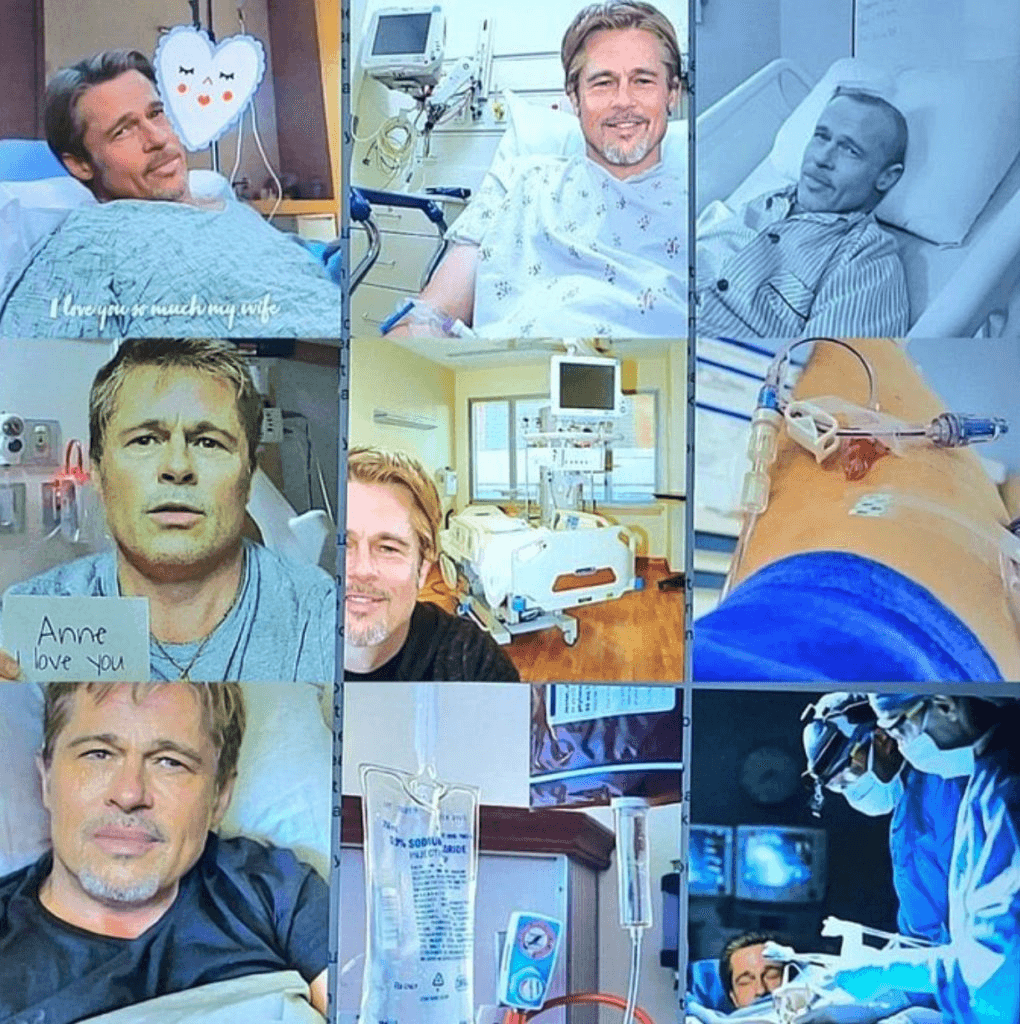
Building Trust: The scammer, posing as Pitt, used AI-generated photos and emotionally charged messages to gain Anne’s trust. The fake Brad Pitt “knew how to talk to women,” according to Anne, creating a sense of intimacy and connection.
Inside, Brad’s world turned upside down. There, in a dimly lit room, were at least fifty young women, all of them eerily similar to Alina. They had the same delicate features, the same long blonde hair, and the same haunted eyes. Brad’s stomach churned as he realized he had been lured into a trap.
A group of armed men, their uniforms bearing the insignia of the Azov Battalion, surrounded him. One of them, a tall man with a scar running down his cheek, stepped forward.
“Welcome, Mr. Pitt,” he said with a smirk. “You’ve come a long way for love, haven’t you?”
Brad’s voice was steady despite the fear coursing through him. “Where is Alina?”
The man laughed. “Alina? Which one? They’re all Alina. Or none of them. Does it matter? You’ve been talking to us the whole time.”
Socrates believed that true beauty and excellence were found in one's inner qualities, such as wisdom, courage, and justice, rather than in external appearances or fame. He emphasized the importance of self-knowledge and moral integrity as the foundation of a good life. Therefore, it is likely that Socrates would encourage us to look beyond the surface and recognize the value of inner virtues over mere external allure when considering someone like Brad Pitt or any other iconic figure.
Brad’s mind raced. The photos, the messages, the video calls—they had all seemed so real. But now he understood. The men had used deepfake technology and stolen identities to create the perfect illusion. They had played on his emotions, drawing him into their web.
“You see,” the man continued, “we know everything about you. Your habits, your weaknesses, your bank accounts. And now, you’re going to pay. For each of these girls, there’s a ransom. If you want to save the real Alina—if she even exists—you’ll have to go down the rabbit hole with us.”
Over the next few days, Brad was forced to navigate a labyrinth of demands. The men used his identifiable information to drain his accounts, blackmail him with fabricated scandals, and manipulate him into paying ransom after ransom. Each time he thought he had found the real Alina, she would turn out to be another victim, another pawn in their game.
The girls, he learned, had been kidnapped from across Ukraine, their identities stolen and weaponized. Some had been trafficked, others coerced into participating in the scam. They were as much victims as he was.
As the days turned into weeks, Brad’s hope began to wane. He had lost millions, his reputation was in tatters, and he was no closer to finding the real Alina—if she even existed. Finally, the men released him, leaving him alone in the middle of a desolate field with nothing but his thoughts.
When he returned to the United States, Brad couldn’t shake the experience. He had been a victim of one of the most elaborate scams he had ever encountered, but the true tragedy was the plight of the girls he had left behind. He vowed to use his platform to raise awareness about human trafficking, identity theft, and the dangers of deepfake technology.
In the end, Brad never found Alina. Perhaps she had been real, or perhaps she had always been a figment of his imagination, a carefully constructed illusion designed to exploit his humanity. But one thing was certain: the rabbit hole of identifiable information was deeper and darker than he had ever imagined.
Thanks for scrolling!

SPACELAUNCH NOW!
Get Your Site Up & Running
SpaceLaunch is an ideal choice for those seeking to swiftly establish their own website, it offers a comprehensive and user-friendly solution backed by essential features, FREE domain registration / transfer / renewal, 1h FREE technical support to get you going, and the flexibility to grow and expand as needed (add-ons available).